Cisco TrustSec – ISE (Part 4)
Configure Network Access Device (NAD)
Configure Network Access Device (NAD)
2960S Sample Configuration
aaa new-model
!
aaa authentication login noise line none
!
line con 0
login authentication noise
!
radius-server host 202.100.1.241 key cisco
!
snmp-server group baiminggroup v3 priv
snmp-server user baiminguser baiminggroup v3 auth md5 12345678 priv des 87654321 snmp-server enable traps
snmp-server host 202.100.1.241 version 3 priv baiminguser
Add Network Device Groups(NDG)
Setup privileges based on device locations and device types;
Add Network Device(AAA Client)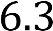
PS:The reason why crate Device group is to define different polices based on locations.
Fill in 2960S Radius Key and SNMP info;
6.3.1 Test Radius Connectivity
6.3.1.1 Change default user password policy
Add user
Recommended Switch Configuration
aaa new-model
aaa authentication dot1x default group radius aaa authorization network default group radius
aaa accounting dot1x default start-stop group radius
---Enable AAA DO1X
aaa server radius dynamic-author client 202.100.1.241 server-key cisco
---enable CoA (Change of Authorization)
dot1x system-auth-control
---Global enable Dot1X
ip device tracking
---Trace IP
radius-server attribute 6 on-for-login-auth
---Send the Service-Type attribute in access requests
radius-server attribute 8 include-in-access-req
---Send the Framed-IP-Address attribute in access requests
radius-server attribute 25 access-request include
---Send the Class attribute in access requests
radius-server dead-criteria time 5 tries 3
---Wait 3 x 5 seconds before marking RADIUS server as dead
radius-server host 202.100.1.241 key cisco radius-server vsa send accounting
---Enables vendor-specific attributes to be sent in RAIDUS accounting messages
radius-server vsa send authentication
---In order to enable dACLs, you must first configure your access switch to allow communications using the cisco-av-pair attribute with the valus aaa : event=acl-download. Enter the command shon here in the global configuration of the switch. If you fail to add this command, will result in
failed authentication/authorization requests.
ip access-list extended ACL-DEFAULT remark DHCP
permit udp any eq bootpc any eq bootps remark DNS
permit udp any any eq domain remark Ping
permit icmp any any remark TFTP
permit udp any any eq tftp remark Drop all the rest deny ip any any log
---permit basic traffic
!
ip access-list extended WEB-REDIRECT deny udp any any eq domain
deny udp any host 202.100.1.241 eq 8905 deny udp any host 202.100.2.254 eq 8905 deny udp any host 202.100.1.241 eq 8906 deny udp any host 202.100.1.241 eq 8909 deny tcp any host 202.100.1.241 eq 8443
deny tcp any host 202.100.1.241 eq 8905 deny tcp any host 202.100.2.254 eq 8905 deny tcp any host 202.100.1.241 eq 8909 permit ip any any
---redirect web traffic
interface GigabitEthernet1/0/1 description ISE-MAB-DOT1X-WEBAUTH switchport access vlan 2
switchport mode access
ip access-group ACL-DEFAULT in
authentication event fail action next-method
authentication event server dead action authorize vlan 10
authentication event server alive action reinitialize
authentication host-mode multi-auth
authentication open
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication violation restrict
mab
dot1x pae authenticator
No comments:
Post a Comment